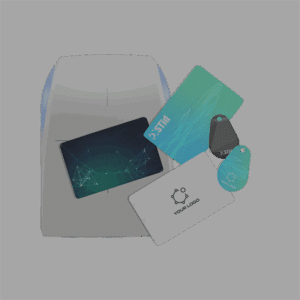
Evolve Without Constraints
What if you could turn the challenges of technological migration into opportunities? With 70% of access control systems outdated and vulnerable, upgrading is essential to protect people and assets against physical and cyber threats.
However, transitioning an installed system while maintaining continuity of service is no easy task. At STid, we help you navigate this journey step by step, ensuring an effective, scalable, and end-to-end security solution—from installation to data management and control.
Define a Comprehensive Migration Strategy
Plan for Today’s Challenges and Tomorrow’s Threats
Our expert teams collaborate with you to define a strategy tailored to your specific requirements and potential risks. This includes:
- Identifying vulnerabilities in your current system.
- Analyzing constraints to ensure a smooth transition.
- Deploying interoperable and sustainable solutions to secure badges, readers, and communication protocols.
Our Comprehensive Approach
As the visible entry point to your system, the reader is also the first target for attackers. A secure reader should:
- Badges + Stickers + Smartphone: Transition from outdated 125kHz or MIFARE Classic to advanced technologies like DESFire EV3 or STid Mobile ID for virtual badges. Discover
- Readers + Modular Upgrades: Upgrade to ARCHITECT readers with plug-and-play modules for scalable security. Discover
- Protocols + Easy Secure/Remote Interfaces: Migrate to encrypted protocols like SSCP or use our migration interfaces to secure legacy systems without disrupting operations. Discover
Replace Obsolete Badges
Defend the First Line of Security
Outdated badges like 125kHz or MIFARE Classic are easily cloned within seconds, making them a prime vulnerability. Replace these with:
- DESFire EV3 or STid Mobile ID virtual badges for advanced encryption.
- Stickers for a cost-effective transition while retaining legacy devices.
Upgrade Reader Security
Protect the Most Visible Part of Your System
Obsolete readers leave data unprotected and are easily bypassed. As a key element of access control, they’re a primary target for attackers.
Secure your system with readers featuring:
- Tamper detection and automatic security key erasure.
- Protection through EAL5+ secure elements.
- Compliance with advanced security protocols like SSCP or OSDP SC.
Secure Communication Protocols
Achieve End-to-End Security
An outdated communication protocol with insufficient or no encryption exposes your system to attacks. STid enables secure migration without requiring major system changes:
- Use Easy Secure or Easy Remote interfaces to upgrade to encrypted protocols.
- Transition to SSCP, one of the world’s most secure protocols, for bidirectional communication and seamless management.
Key Highlights
The Benefits of a Controlled Migration
- Migrate seamlessly without disrupting continuity of service.
- Upgrade with modular solutions, avoiding costly replacements.
- Ensure your system is future-proof with scalable technologies.
Why Secure Protocols Matter
Unsecured communication leaves critical data vulnerable. Encrypted protocols like SSCP and OSDP SC protect against interception, ensuring your system’s integrity.
Our History, Your Security
Since 1996, STid has pioneered security innovation with the belief that security is a fundamental right.
- First manufacturer in France to receive CSPN certification.
- Recognized globally for the Architect range, the most awarded readers worldwide.
- Committed to designing instinctive, interoperable, and scalable solutions that empower sovereignty and independence for our users.
A Migration Tailored to Your Needs
- Replace vulnerable technologies to fortify your system.
- Upgrade readers and protocols for advanced protection.
- Migrate seamlessly with solutions that ensure continuity of service.
- Future-proof your system with scalable, open technologies.
NOTRE OFFRE

CREDENTIALS

READERS
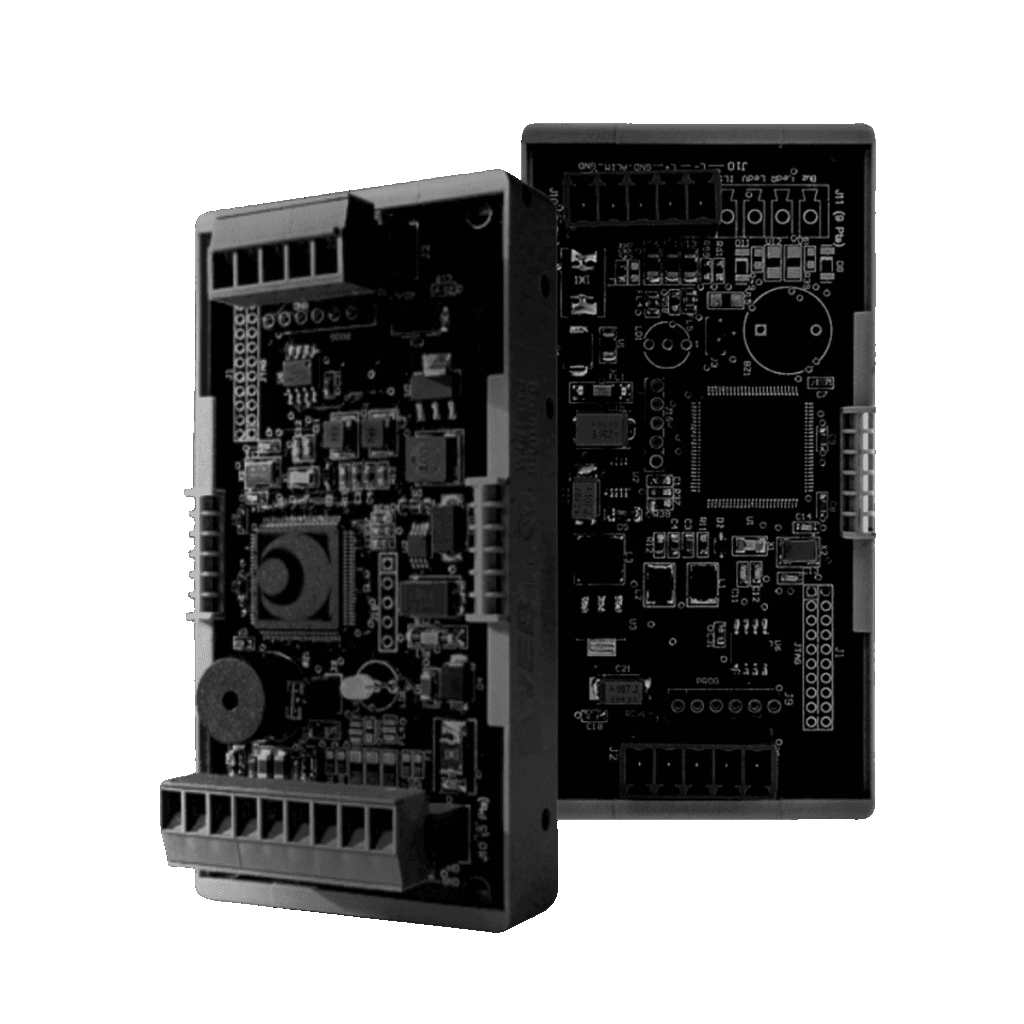
SMART INTERFACE

STid on Field
Our solutions are used every day across the world to address a wide range of challenges—often far beyond simple identification. Thanks to the creativity of our clients and partners, they power innovative, sometimes unexpected applications that transform everyday experiences and deliver real value in the field. Discover how our technologies are integrated into concrete projects to enhance security, streamline operations, and improve user experience.